Compliance
Last Updated October 8, 2023
Introduction
At Every8.Cloud , we proudly serve a wide range of customers, encompassing sectors with regulatory requirements. Through our collaborative responsibility approach, we're dedicated to helping our users expertly navigate and manage IT-related risks. We stand by our commitment to risk management, consistently aligning with recognized frameworks and standards. This document explains the measures Every8.Cloud employs for risk management and offers resources to our customers, ensuring they can confidently leverage our platform to its fullest potential.
Every8.Cloud and its users work together to manage the environment, emphasizing that security is a joint effort. The exact roles in ensuring security and meeting compliance on the Every8.Cloud Platform depend on the specific apps each customer uses. In simple terms, customers need to tailor their usage and implementation of Every8.Cloud apps to their specific security and regulatory needs.
Shared Responsibility Model
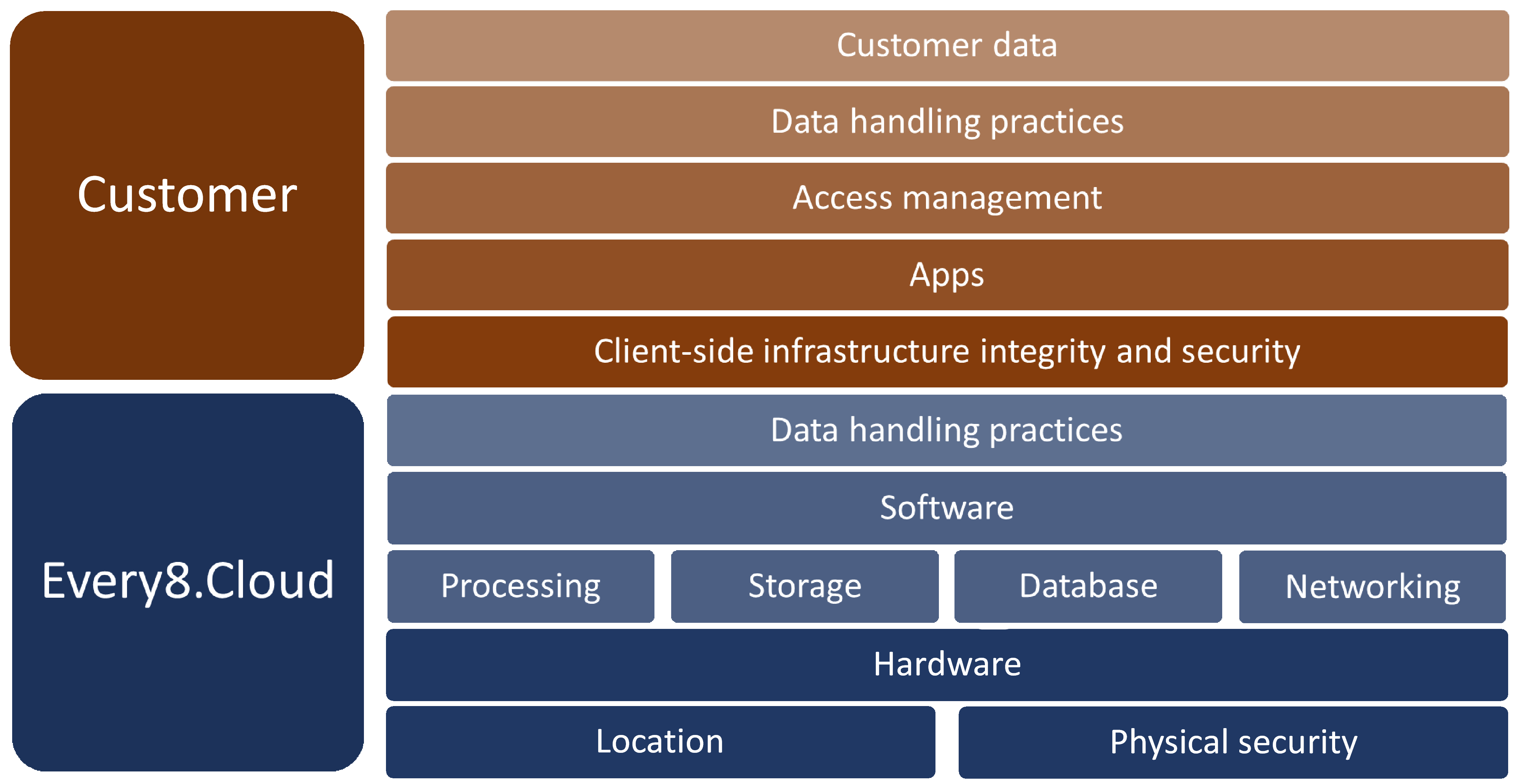
Security and compliance on Every8.Cloud are collaborative efforts between the platform and its customers.
Every8.Cloud oversees, administers, and ensures the security of components from the foundational layers up to the main operational layers.
Meanwhile, customers manage aspects related to their specific apps, user access management, specific business workflows, and configurations within the security parameters provided by the Every8.Cloud Platform.
This joint responsibility model offers the adaptability and control that allows customers to implement solutions that align with sector-specific requirements and regulations.
This diagram demonstrates the shared responsibility between Every8.Cloud and the Customer.
Hardware and Data Location
Every8.Cloud operates a complex server infrastructure that may be located in various countries and regions. The fundamental principle for customer data location is as follows: the customer's country or region is aligned with the closest geographical area where an Every8.Cloud infrastructure exists. With few exceptions, customer data does not leave their own country. Exceptions are made when there's no infrastructure in the customer's country or for organizations conducting business across multiple regions.
If you have any doubts regarding the location of your data, please contact us for detailed information on this matter.
Hardware Physical Security
All our infrastructure is housed in enterprise-grade secure data centers with restricted access to ensure the physical security of the data.
Processing
When data is actively engaged in data processing scenarios, the Every8.Cloud Platform transfers this data into the memory of one or more service tasks. While in memory to support these tasks' functions, the data remains unencrypted.
During these tasks, data is processed by Every8.Cloud 's internal functions and APIs within a highly segregated logical environment.
Storage
Given that encryption places a certain load on the server and considering that most of our clients do not require this level of security by default, files that are part of client data are not encrypted. However, we offer additional options that allow you to activate this feature on the Every8.Cloud Platform.
Please contact us for detailed information on this matter.
Database
Similar to file storage, the default delivery of the Every8.Cloud Platform does not include database table encryption. However, we offer additional options that allow you to activate this feature on the Every8.Cloud Platform. This feature is also known as data at rest encryption.
Please contact us for detailed information on this matter.
Data may be temporarily stored on mobile devices using their local database. Upon logging out, this database is cleared, requiring data to be redownloaded from the servers during the next session.
Networking
The Every8.Cloud Platform requires the use of TLS 1.2 or above for all HTTP traffic. Any requests attempting to utilize TLS 1.1 or below are rejected. This standard applies to traffic from the customer to the Every8.Cloud infrastructure and to the traffic between Every8.Cloud 's internal services.
Every8.Cloud Data Handling Practices
Every8.Cloud is dedicated to maintaining the highest levels of trust, transparency, adherence to standards, and regulatory compliance.
Every8.Cloud processes the customer’s data solely based on the customer’s consent and in accordance with the specific policies and procedures to which Every8.Cloud has contractually committed. Every8.Cloud neither shares the customer’s data with services supported by advertisers nor uses it for marketing research or advertising purposes.
The nature of Every8.Cloud services implies access to customer data. All staff members granted access to customer data undergo training based on the industry's best practices. Any tasks involving access to customer data are logged and monitored.
Customer Compliance Governance
Every8.Cloud customers bear the responsibility for overseeing their IT environment.
Best practices encompass:
- Knowing and understanding the compliance goals and rules.
- Setting up a control environment that matches those goals and rules.
- Recognizing the validation needed in line with the organization's risk acceptance.
- Verifying the effectiveness of their control environment.
Client-side Infrastructure Integrity and Security
Customers must ensure they implement the necessary technologies and policies to safeguard end users from potential threats on dynamic web pages accessed via the user's device. This involves managing web browser versions, utilizing firewalls, deploying antivirus software, monitoring plugins that might capture keyboard inputs, and addressing other elements that could compromise data integrity and processes.
Apps
The Every8.Cloud Platform offers access to a variety of apps available for installation via the Marketplace, as well as the ability to develop custom apps. The Customer should understand the functionality of all apps used by the company and be aware of potential risks associated with their overall use and any misuse.
Access Management
Access control to the system is managed at the platform level, while access control to information within apps is managed through a role-based security mechanism within each app. Customers should understand the access limits of each security role used in the app and recognize the risks associated with incorrectly assigning a role to a user. To maintain control, this process should be documented and regularly audited. Documentation on the process of adding new users and removing departed employees should also undergo regular customer audits.
The Every8.Cloud Platform allows to set password complexity constraints. Any required additional constraints should be outlined in the customer's security policy. Every8.Cloud allows the use of two-factor authentication for system access. While this option is optional, it is highly recommended for companies operating in regulated industries.
Data Handling Practices
The data belongs to the customer. The customer has the freedom to access, modify, or delete it at any time. Every8.Cloud will never use the customer's data without their consent. When given that consent, we utilize the data exclusively to provide the services the customer has selected. While Every8.Cloud provides a robust platform to manage and store data, it is essential for customers to fully understand the significance of consistently implementing and reinforcing security policies that oversee data utilization within their organization.
Customer Data
Customer should recognize the importance of regularizing and enforcing security policies that govern data usage within the company. Users must understand that they operate in a shared environment and be aware of which information should not be accessible within certain data objects of the apps. This pertains to personal data, credit card details, and the like.
How Every8.Cloud Uses Data to Improve Service
Every8.Cloud leverages customer data for troubleshooting, aiming to proactively identify, address, and rectify issues that could disrupt the operation of Every8.Cloud services. Our team is continuously refining and advancing features to improve the reliability and protection of both services and data.
Data Management Upon Service Termination
Should the customer opt to discontinue using Every8.Cloud , the customer data is thoroughly removed from our systems, storage resources are overwritten before they are repurposed, and any decommissioned hardware is thoroughly purged or destroyed.